Zero Trust Security An Enterprise Guide Pdf Zero Trust is about fundamentally changing the underlying philosophy and approach to enterprise security moving from outdated and demonstrably ineffective perimeter centric approaches to a
Title Zero Trust Security An Enterprise Guide Author s Jason Garbis Jerry W Chapman Release date February 2021 Publisher s Apress ISBN 9781484267028 Understand how Zero Trust security can and should integrate into your organization This book covers the complexity of enterprise environments and provides the realistic guidance A Zero Trust security framework also dictates that only authenticated and authorized users and devices can access applications and data At the same time it protects those applications and users from advanced threats on the Internet To progress on your Zero Trust journey safeguarding users applications and the future of your
Zero Trust Security An Enterprise Guide Pdf
 Zero Trust Security An Enterprise Guide Pdf
Zero Trust Security An Enterprise Guide Pdf
https://questsys.com/wp-content/uploads/2021/05/Zero-Trust_Blog-Graphic_Final.jpg
2022 TLDR This survey compares the novel requirement specific features used by state of the art research models for zero trust cloud networks focusing on domain specific issues plaguing modern cloud computing networks which leverage choosing and implementing features necessary for future networks and incorporate intelligent security
Templates are pre-designed files or files that can be utilized for various functions. They can save effort and time by offering a ready-made format and layout for developing various type of material. Templates can be used for personal or professional jobs, such as resumes, invitations, flyers, newsletters, reports, presentations, and more.
Zero Trust Security An Enterprise Guide Pdf

What Is A Zero Trust Security Model JumpCloud

Secure Your Network With Zero Trust CGNET Cyber Security

Zero Trust Data Security Sightline Systems Monitoring And Analytics

Zero Trust Setting The New Standard For Enterprise Security But It
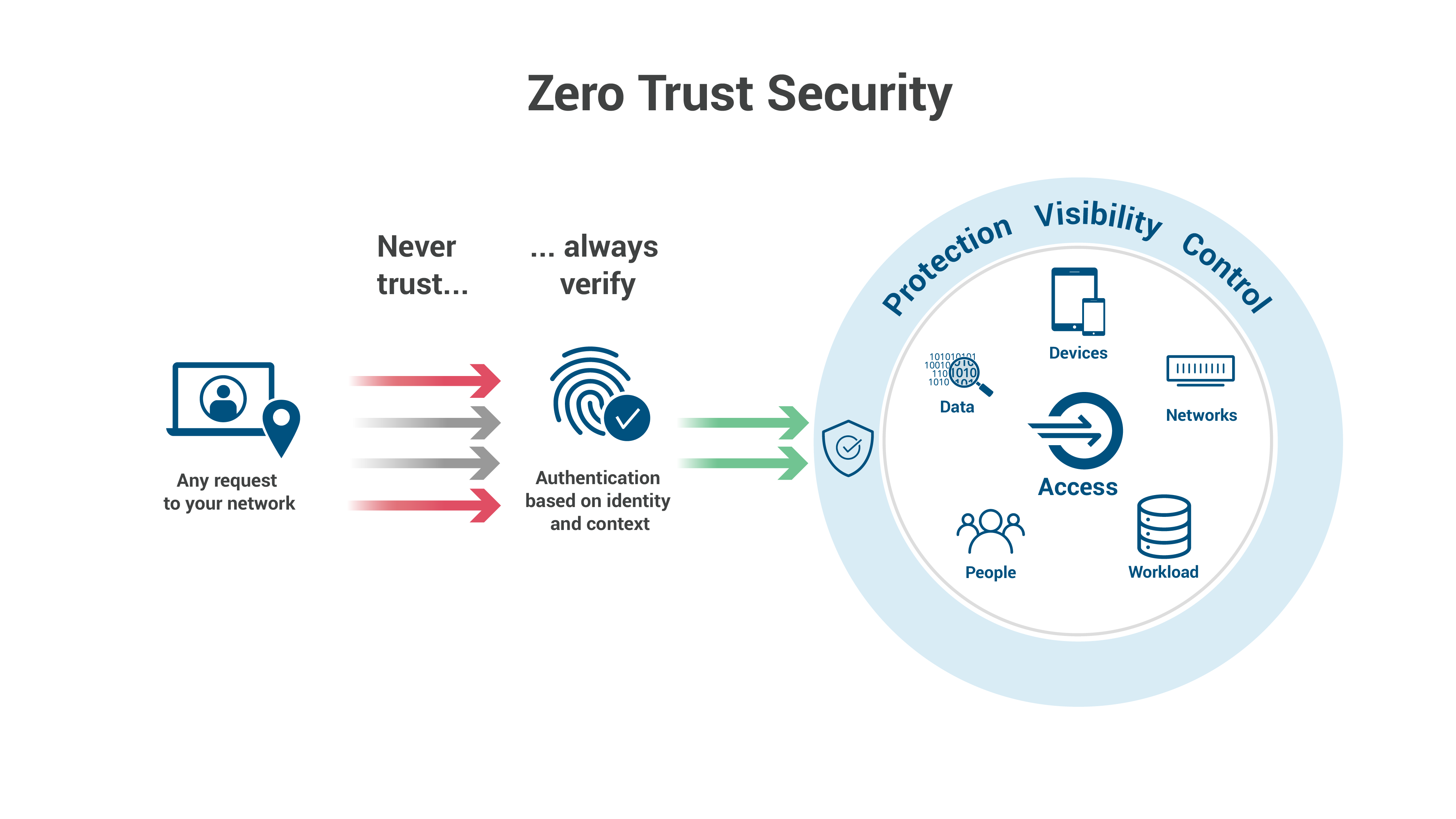
Appgate Es Destacado En Un Nuevo Informe T cnico Sobre Zero Trust ITSitio

Zero Trust Security Model Rethinking IT Asset Security CVP

https://link.springer.com/book/10.1007/978-1-4842-6702-8
Jason Garbis is Founder and Principal at Numberline Security a consulting firm helping enterprises prepare for define and execute on effective Zero Trust security strategies Jason has authored several books including Zero Trust Security An Enterprise Guide and Getting Started With Zero Trust He is co chair of the Zero Trust Working Group at the Cloud Security Alliance and is a

https://www.cisa.gov/sites/default/files/publications/Zero_Trust_Principles_Enterprise_Mobility_For_Public_Comment_508C.pdf
Is an enterprise s cybersecurity plan that utilizes zero trust concepts and encompasses component relationships workflow planning and access policies Therefore a zero trust enterprise is the network infrastructure physical and virtual and operational policies that are in place for an enterprise as a product of a zero trust architecture

https://csrc.nist.gov/CSRC/media/Presentations/zero-trust-architecture-101/images-media/Zero%20Trust%20Architecture%20101%20-%20Scott.pdf
Zero Trust Architecture Initiative Tenets of Zero Trust All enterprise systems are considered resources The enterprise ensures all owned systems are in their most secure state possible All communication is done in a secure manner regardless of network location Access to individual enterprise resources is granted on a per connection basis

https://www.nist.gov/publications/zero-trust-architecture
Zero trust ZT is the term for an evolving set of cybersecurity paradigms that move defenses from static network based perimeters to focus on users assets and resources A zero trust architecture ZTA uses zero trust principles to plan industrial and enterprise infrastructure and workflows Zero trust assumes there is no implicit trust

https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.20.pdf
Implementation or architecture zero trust solutions depend on the workflow i e part of the enterprise mission being analyzed and the resources that are used in performing that workflow zero trust strategic thinking can be used to plan and implement an enterprise IT infrastructure this plan is called a zero trust architecture ZTA
NIST Special Publication 800 207 defines zero trust as a set of cybersecurity principles used when planning and implementing an enterprise architecture These principles apply to endpoints services and data flows Input and cooperation from various stakeholders in an enterprise is needed for a zero trust architecture to succeed in improving the enterprise security posture Some of these Zero Trust is a security model a set of system design principles and a coordinated cybersecurity and system management strategy based on an acknowledgement that threats exist both inside and outside traditional network boundaries The Zero Trust security model eliminates implicit trust in any one element node or service and instead
Aid understanding of zero trust for civilian unclassified systems and provide a road map to migrate and deploy zero trust security concepts to an enterprise environment Agency cybersecurity managers network administrators and managers may also gain insight into zero trust and ZTA from this document