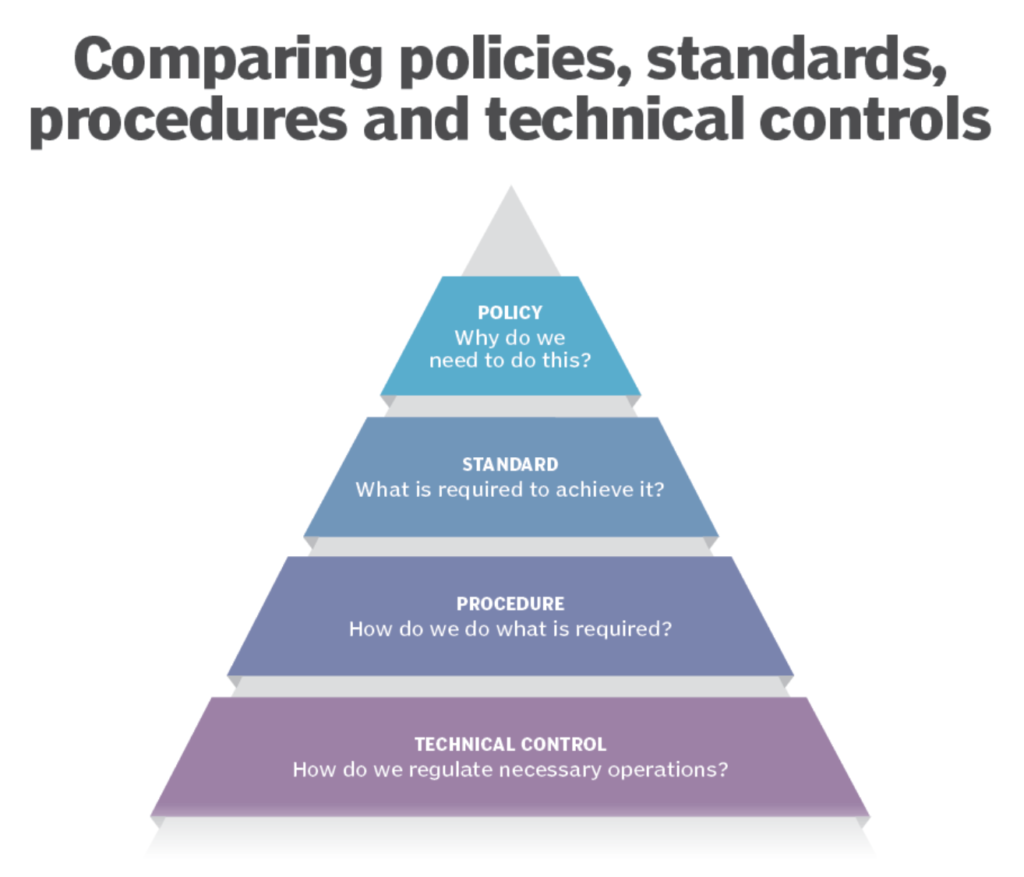
Security Configuration Standards A security configuration checklist also called a lockdown hardening guide or benchmark is a series of instructions or procedures for configuring an IT product to a particular operational environment for verifying that the product has been configured properly and or for identifying unauthorized changes to the product The IT product may be
Effective security of other than national security related information in federal information systems The Special Publication 800 series reports on ITL s research guidelines and outreach efforts in information systems security and privacy and its collaborative activities with industry government and academic organizations Abstract PK l Content Types xml O 0 N 4 7 w B tk x s x w nY H n Ul 8Or V p R h A 6 l Z qK Wm Y E HD FK z 5 2 lj J I lu Q nD R
Security Configuration Standards
 Security Configuration Standards
Security Configuration Standards
https://i.pinimg.com/originals/4a/4d/b2/4a4db2ac5c5dba707f392566361d2f9d.png
Microsoft the Center for Internet Security CIS the National Security Agency NSA the Defense Information Systems Agency DISA and the National Institute of Standards and Technology NIST have published security configuration guidance for Microsoft Windows
Pre-crafted templates offer a time-saving service for producing a diverse range of documents and files. These pre-designed formats and layouts can be utilized for various personal and professional jobs, consisting of resumes, invites, leaflets, newsletters, reports, presentations, and more, streamlining the material production procedure.
Security Configuration Standards

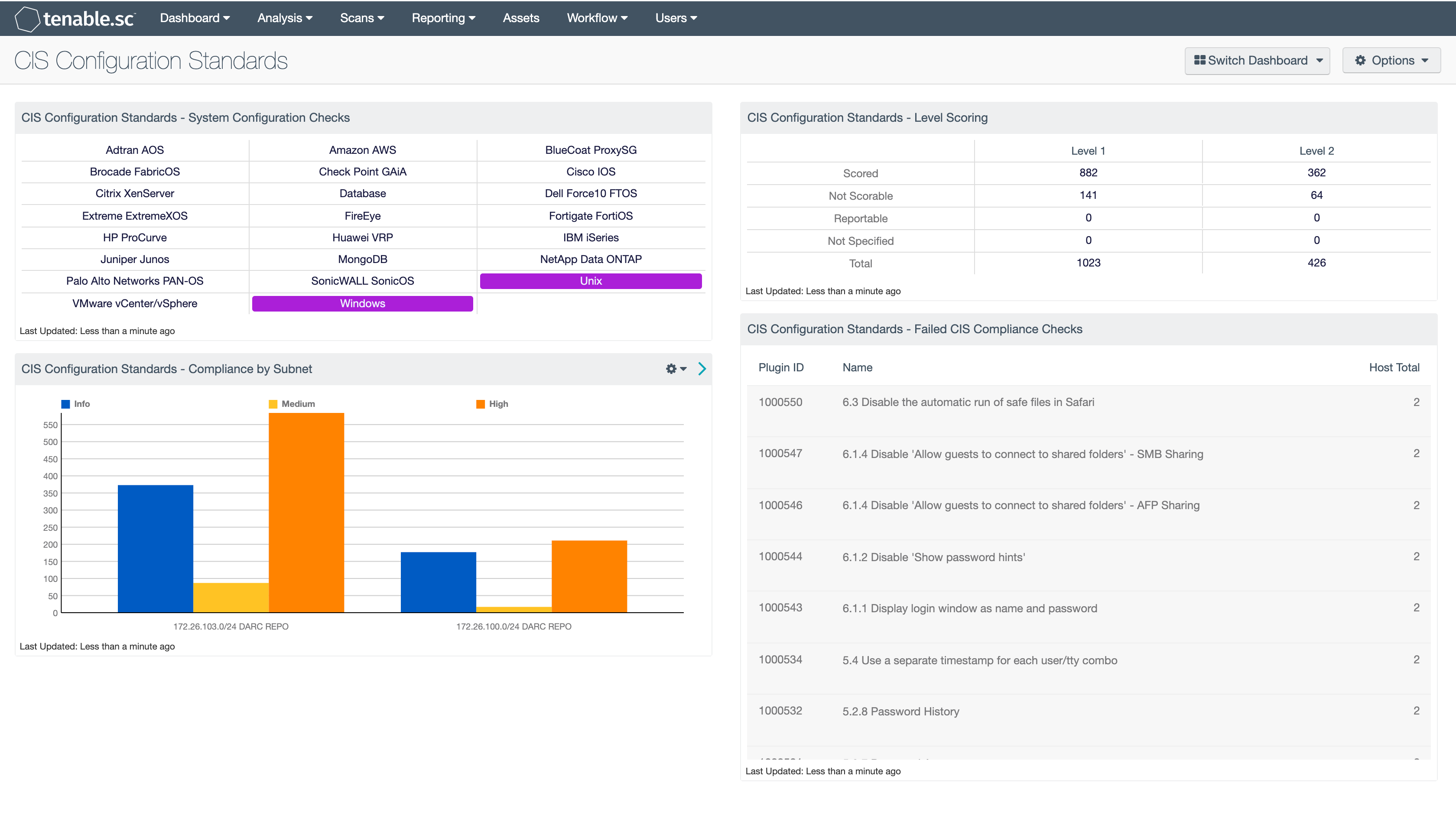
Security Configuration Assessment SCA Wazuh

Data Security Practices You Didn t Know About Hitachi Systems Security

Security Configuration Management This Is Why It Is So Important For

Products Koehler Instrument Company Inc

PDF Solutions Enabler Security Configuration Guide Security

CSM Security Bungalow QLD

https://csrc.nist.gov/pubs/sp/800/128/upd1/final
The purpose of Special Publication 800 128 Guide for Security Focused Configuration Management of Information Systems is to provide guidelines for organizations responsible for managing and administering the security of federal information systems and associated environments of operation
https://its.fsu.edu/cybersecurity/standards/it-security-configuration-management-standard
Security Configuration Management the management and control of configurations for an information system with the goal of enabling security and managing risk The process includes identifying controlling accounting for and auditing changes made to pre established Baseline Configurations Full IT Glossary III Standard
https://csrc.nist.gov/Projects/United-States-Government-Configuration-Baseline
The purpose of the United States Government Configuration Baseline USGCB initiative is to create security configuration baselines for Information Technology products widely deployed across the federal agencies The USGCB baseline evolved from the Federal

https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-123.pdf
National Institute of Standards and Technology nor is it intended to imply that the entities materials or equipment are necessarily the best available for the purpose Using security configuration guides or checklists can assist administrators in securing servers consistently and efficiently Securing an operating system

https://csrc.nist.gov/Projects/National-Checklist-Program
A security configuration checklist also called a lockdown hardening guide or benchmark is a series of instructions or procedures for configuring an IT product to a particular operational environment for verifying that the product has been configured properly and or for identifying unauthorized changes to the product
Establish and maintain a secure configuration process CIS configuration standards involve the development and application of a strong initial configuration followed by continuous management of your enterprise assets and tools These assets include Laptops workstations and other user devices The security configuration framework is designed to help simplify security configuration while still allowing enough flexibility to allow you to balance security productivity and user experience We are defining discrete prescriptive Windows 10 security configurations levels 5 through 1 to meet many of the common device scenarios we see today in the enterprise
The next version of the control set incorporates all or part of this control into 4 1 Establish and Maintain a Secure Configuration Process Control Statement Maintain documented security configuration standards for all authorized operating systems and software